From our front-page news:
If there's an interesting method of making some cash, someone is bound to figure out how to execute it to the best of their ability. Over the years, we've heard of stories where someone would code up a robust virus/trojan, release it, and then do horrible things to people's computers. The catch is that the data seemingly ruined by this malware isn't actually ruined, but can be recovered if the user wants to pay a ransom fee.
As horrible as that practice is, I can't help but laugh at it's ingenuity. Ten years ago, I would have never thought of data being held for ransom, as if it were a person, but it's rather common today. Someone in the Netherlands took a very similar route recently, but there's an interesting twist... he had no intention of damaging or ruining people's data, but rather demands cash for the solution on how they could secure themselves.
The product in question is none other than the iPhone, in a jailbroken status. Apparently, there's a security hole somewhere that can allow a cracker to get in and essentially take over the entire phone, including personal data. As you can see in the screenshot below, the words "hacked" are listed at the top. There's also a message that centers itself on the screen that states that the phone's security has been circumvented, and that this person has full access to all the files.
It's not all bad, because should the user want to regain their security, a URL is given. Although down now, the page requested $7 to be sent to a PayPal account, at which point this person would e-mail the victim to explain how to better secure their iPhone. Since this news broke, though, the person had a change of heart and decided to tell everyone how to fix their jailbroken iPhone with a few simple steps, which you can find here. Hopefully this event is one of the very few we'll see happen. With the insane popularity of mobile phones though, something tells me this is just the beginning.
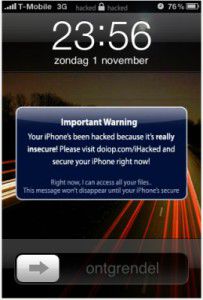
Apparently, the hacker used port scanning to identify phones on the T-Mobile network in the Netherlands running SSH (Secure Shell network protocol), which is commonly used by jailbroken iPhones and allows a user to "log in via Terminal and run standard UNIX commands," according to Ars Technica. iPhone users who don't change the default root password after jailbreaking the device leave the phones vulnerable to attack, the site said.
Source: InSecurity Complex
As horrible as that practice is, I can't help but laugh at it's ingenuity. Ten years ago, I would have never thought of data being held for ransom, as if it were a person, but it's rather common today. Someone in the Netherlands took a very similar route recently, but there's an interesting twist... he had no intention of damaging or ruining people's data, but rather demands cash for the solution on how they could secure themselves.
The product in question is none other than the iPhone, in a jailbroken status. Apparently, there's a security hole somewhere that can allow a cracker to get in and essentially take over the entire phone, including personal data. As you can see in the screenshot below, the words "hacked" are listed at the top. There's also a message that centers itself on the screen that states that the phone's security has been circumvented, and that this person has full access to all the files.
It's not all bad, because should the user want to regain their security, a URL is given. Although down now, the page requested $7 to be sent to a PayPal account, at which point this person would e-mail the victim to explain how to better secure their iPhone. Since this news broke, though, the person had a change of heart and decided to tell everyone how to fix their jailbroken iPhone with a few simple steps, which you can find here. Hopefully this event is one of the very few we'll see happen. With the insane popularity of mobile phones though, something tells me this is just the beginning.

Apparently, the hacker used port scanning to identify phones on the T-Mobile network in the Netherlands running SSH (Secure Shell network protocol), which is commonly used by jailbroken iPhones and allows a user to "log in via Terminal and run standard UNIX commands," according to Ars Technica. iPhone users who don't change the default root password after jailbreaking the device leave the phones vulnerable to attack, the site said.
Source: InSecurity Complex
